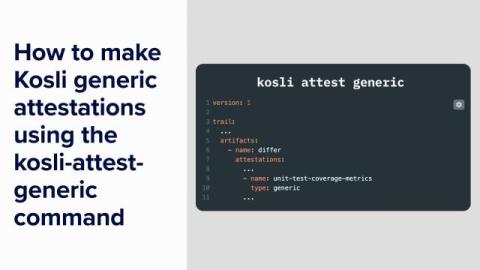
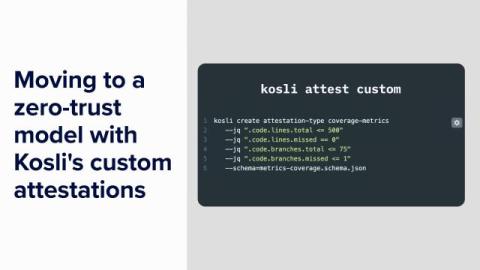
Enterprise-Grade Software Security: Mastering Control Over Your Software IP
Enterprises should prioritize securing their software artifacts to protect intellectual property (IP), maintain compliance, and mitigate supply chain risks. A strong security posture requires a deep understanding of access management, distribution controls, compliance enforcement, and software lifecycle governance.