Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
SIEM Logging for Enterprise Security Operations and Threat Hunting
Today's enterprise networks are diverse and complex. Rather than the simple network perimeter of old, bad actors can attack through multiple entry points, including cloud-based applications. Not to mention, these networks generate massive amounts of transactional data. Because enterprise networks have become larger, they're more difficult to secure and manage. As a result, IT operations teams and security analysts seek better ways to deal with the massive influx of information to improve security and observability.
Migrating from Travis to Github Actions
For CFEngine we manage several public and private repositories of code in GitHub for our Open Source and Enterprise products. In order to ensure quality we run many checks on the code both with nightly builds as well as on each pull request. We use a Jenkins server for nightlies which also includes more extensive deployment tests on all of the platforms we support. Previously we had used Travis for many of these checks but that system started to show its age and limitations.
Discovering Zero Days: Why configuration management wins
“Zero Days” may be one of the most recognizable cybersecurity terms, other than hacker of course, for good reason. Zero Day Vulnerabilities are notoriously challenging for defending security teams to identify. Because of delays between active exploit and discovery, they are one of the worst examples of “Known Unknowns” in cybersecurity (Other than user’s behavior of course..). It’s important to understand that Zero Days are not really brand-new vulnerabilities.
Streamlining SAP Kernel upgrades with Avantra
Picture the SAP Kernel as the heartbeat of the system, vitalizing the core programs upon which the fundamental functionality of SAP applications rely on. It's the life force pulsing through the application server, executable programs, database, and operating system, rather than merely encompassing them within itself. SAP Kernel upgrades refer to updating the system's current executables with upgraded versions. These upgrades are essential to patch security vulnerabilities and fix bugs. Besides bug fixing, SAP Kernel upgrades improve hardware compatibility, boost speed, and enhance stability.
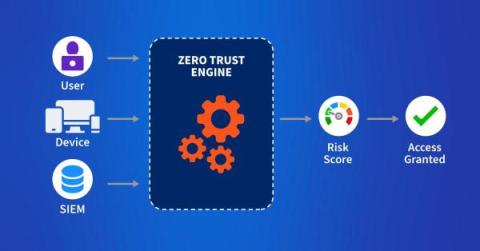
How to Harden Zero-Trust Cloud Network Policy with Kentik
Zero trust in the cloud is no longer a luxury in the modern digital age but an absolute necessity. Learn how Kentik secures cloud workloads with actionable views of inbound, outbound, and denied traffic.
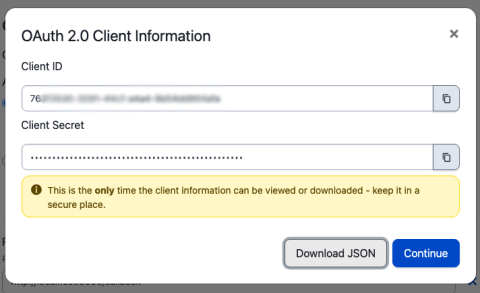
Build Sophisticated Apps for Your PagerDuty Environment Using OAuth 2.0 and API Scopes
Many PagerDuty customers create their own apps to help them manage their PagerDuty environments. Teams might have any number of workflows that might benefit from a custom application. A PagerDuty admin might want to be able to load CSV files with new users and their contact information into PagerDuty when new teams join the platform, or load new services before they are released to production.
Proactively secure your business with new Cisco Secure Application enhancements to protect cloud environments
Map, prioritize and act on security issues found in cloud environments with the newly expanded security offering from Cisco AppDynamics. Welcome to the October edition of the What’s New in Security series — and — happy security awareness month!
The DevOps Security and Compliance Guide
The fast-paced nature of modern software development means developers are capable of deploying changes to production multiple times a day. But, while DevOps allows development teams to deliver new features faster, increased deployment frequency can make it more difficult to stay on top of security threats. It only takes one malicious or incompetent change to dramatically increase the risk exposure of an application.
Network Security Best Practices
A guide to maintaining a secure network.