Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
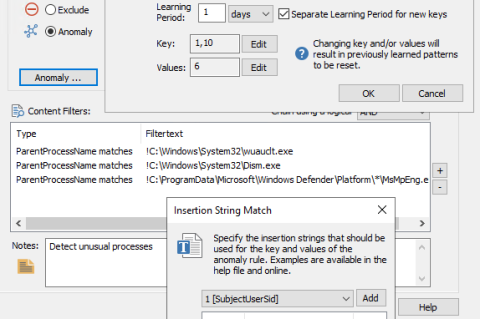
EventSentry v5.1: Anomaly Detection / Permission Inventory / Training Courses & More!
We’re extremely excited to announce the availability of the EventSentry v5.1, which will detect threats and suspicious behavior more effectively – while also providing users with additional reports and dashboards for CMMC and TISAX compliance. The usability of EventSentry was also improved across the board, making it easier to use, manage and maintain EventSentry on a day-by-day basis. We also released 60+ training videos to help you get started and take EventSentry to the next level.
6 Types of Security Incidents and How To Handle Them
Bad news: Cybercrime is surging, emerging AI tools offer hackers new paths of attack, and the ever-present reality of human error frequently exposes private information. The effects of security incidents can wipe out entire businesses. Estimates predict the annual toll of cybercrime and security breaches to reach $10.5 trillion by 2025. But you can still protect your business if you know how to handle and respond to these security incidents.
Okta evolving situation: Am I impacted?
Security in DevOps Best Practices to Keep Your Pipeline Secure
Software development, DevOps practices have become a cornerstone for organizations looking to streamline their processes and deliver high-quality software. While the agility and efficiency DevOps brings to the table are undeniable, it’s essential to remember that security should never be compromised in the pursuit of speed. In fact, it should be an integral part of the entire DevOps lifecycle.
5 Biggest Threats to Encryption
Meeting the SEC's New Cybersecurity Rules: How Flowmon Empowers Public Companies To Comply
The much-anticipated cybersecurity rules by the U.S. Securities and Exchange Commission (SEC) for public companies have arrived, signaling a significant step forward from the proposed rules released in March 2022. These final rules, effective July 26, 2023, introduce new obligations that public companies must adhere to, promising a more secure and transparent corporate landscape. However, these regulations bring significant compliance challenges and litigation risks.
Using Cribl Search to Aid in Threat Hunting by Enriching Data in Motion
Cribl Search is reshaping the data search paradigm, empowering users to uncover and analyze data directly from its source. Cribl Search can easily reach out and query data already collected in Amazon S3 (or S3 compatible), Amazon Security Lake, Azure Blob, Google Cloud Storage, and more. By searching data where it lives, you can dramatically speed up your search process by avoiding the need to move data before analyzing it.
Implementing Backstage 3: Integrating with Existing Tools Using Plugins
This third part of the “Implementing Backstage” series explains how to integrate Backstage with existing tools and plugins. If you’re at an earlier stage of your Backstage implementation, the two previous installments in this series focus on getting started and using the core features. If you’re looking for a more general introduction to Backstage, you can read the first article in the “Evaluating Backstage” series.