Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
How To Stop Norton Spam Emails
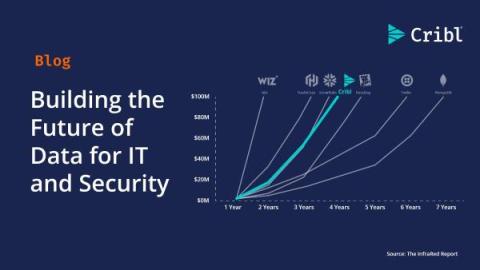
Building the Future of Data for IT and Security
Today, Cribl surpassed $100 million in annual recurring revenue (ARR), becoming one of the fastest companies to ever reach this milestone in under four years––an incredible achievement on our journey to building a generational company. Reaching $100 million in ARR so quickly shows that our unique approach and steadfast focus on IT and Security continues to be validated by the market.
The Dangers Lurking in Open Source Software
Our 1st blog in our series on securely consuming OSS. Today, I'll give an overview of some of the most common types of attacks from consuming OSS. Open-source software (OSS) fuels innovation. Over 96% of commercial applications rely on at least one OSS component (Synopsys, 2023). At Cloudsmith, we champion OSS and understand its indispensable role in today's software landscape. However, the escalating threat of supply chain attacks targeting OSS demands a robust defence.
Staying on the Right Side of HIPAA: Compliance Tips for 2023
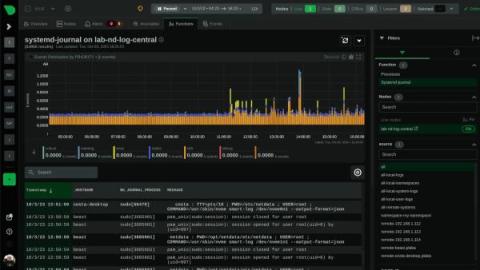
Improve Your Security With systemd-journal and Netdata
systemd journals play a crucial role in the Linux system ecosystem, and understanding the importance of the logs contained within is essential for both system administrators and developers.
Ten modern SIEM use cases
Security Information and Event Management (SIEM) protects organizational assets in today's evolving cybersecurity landscape. As threats become more sophisticated, the importance of well-structured SIEM use cases cannot be underestimated. Dive in as we explore the modern approaches to building, organizing, and prioritizing SIEM use cases. Read on to learn the right approach to building SIEM use casesGathering the Right Data for Meaningful Insights The top ten use cases you cannot afford to miss.
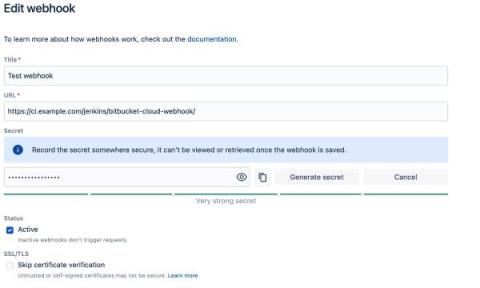
Introducing enhanced webhook security
Optimizing SharePoint Security
In today’s digital-first business landscape, collaborative platforms like Microsoft SharePoint are not merely a convenience but a necessity. They facilitate seamless interaction, information sharing, and collective project management across geographically dispersed teams. However, the enhanced connectivity and accessibility come with a set of security challenges.