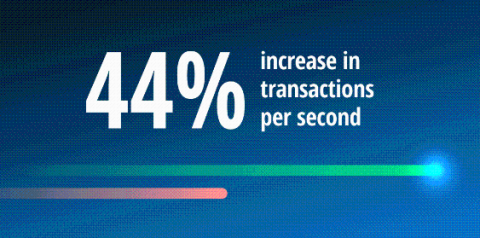
The 3 musts for every FinTech incident management pro
Few industries have experienced such a disruptive whiplash as the financial services industry. With the dizzying encroachment of agile, innovative, and fearless fintechs coming to the fore, traditional banking institutions have had to completely rethink their business, revenue models, and customer engagement initiatives.