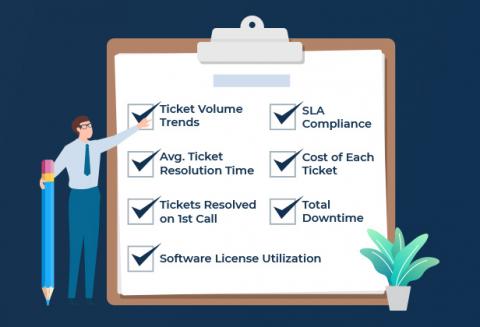
7 Important Service Desk Metrics to Measure
Service desk or IT teams are critical to organisations for ensuring business continuity and service delivery. Hence, it becomes important for IT organizations to use a slew of metrics to measure how efficient their service desk is. With the recent advancement in IT Service Management (ITSM), the reporting capabilities offer multiple KPI metrics that can be measured and monitored. So, with the increase in service desk metrics, it becomes even more difficult to zero down on which metrics to measure.