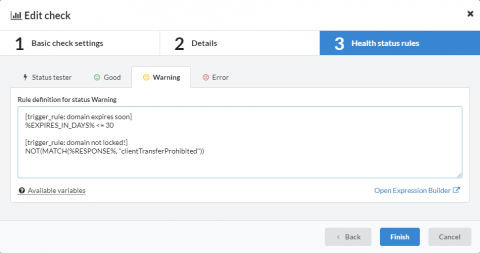
How to monitor your domain Registrar Lock status with AppBeat?
A domain in “Registrar Lock” status means the registrar for that domain has locked the domain to prevent any unauthorized domain transfers / changes. Our domain monitor can check domain expirations but did you now you can also check domain locks?