Operations | Monitoring | ITSM | DevOps | Cloud
Networks
The latest News and Information on IT Networks and related technologies.
HAProxyConf 2019 - Building a Global PoP Network Using HAProxy by Luke Seelenbinder
Active response monitoring: first aid for your services
Monitoring is typically viewed as informative service: when a problem arises, messages are being sent, to alert people in charge to detected problems. However, IPHost Network Monitor allows creating composite alerts, including several so-called simple actions (such as “send mail”, “display pop-up” and so on). These simple actions can be used to proactively react to certain failure conditions – not only to inform of them, but also take measures to handle the actual issues.
Istio vs. Linkerd vs. Envoy: A Comparison of Service Meshes
In a previous article, we examined service meshes in detail. Briefly, a service mesh takes care of network functionality for the applications running on your platform. As Kubernetes has matured as a technology, service meshes have become a hot topic, with various products being developed to solve the challenges associated with areas like traffic management, security, and observability. This article will compare three service meshes.
How to Quickly Identify Suspicious Network Behavior With Intuitive Dashboards in SolarWinds SEM
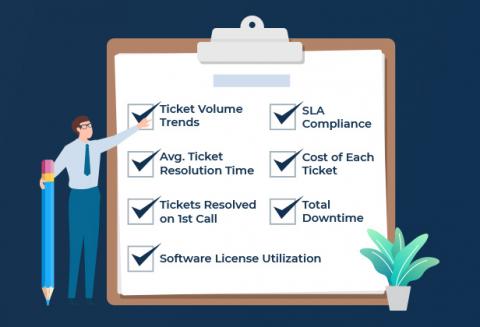
7 Important Service Desk Metrics to Measure
Service desk or IT teams are critical to organisations for ensuring business continuity and service delivery. Hence, it becomes important for IT organizations to use a slew of metrics to measure how efficient their service desk is. With the recent advancement in IT Service Management (ITSM), the reporting capabilities offer multiple KPI metrics that can be measured and monitored. So, with the increase in service desk metrics, it becomes even more difficult to zero down on which metrics to measure.
Security monitoring optimization: typical problems and their solutions
Security issues can be a challenge; preventing them via properly set up monitoring can save many resources. However, as network grows, the list of resources subject to monitoring may grow much faster. A typical situation is a data center: when new hosts (servers) are added, multiple monitors of the same type can be added (depending on server type: Web server, mail server and so on). In such a situation, it is required to reduce possible amount of monitors to as small number as possible.
Application Compatibility Issues Make OS Migration a Headache for 75% of IT Professionals
Make your monitoring efficient: use clear and visible alerts
Default monitoring settings can be quite usable for most use cases; however, as the monitoring setup grows, certain configuration tweaks might be required to make monitoring more efficient. Alerts should actually attract attention of network administrator; otherwise, they are as good as gone. Alerts sent by monitoring tools should reach their destination. Although it can look obvious, there are several common pitfalls we should warn you about.
Three Keys to Automating Enterprise Network Management
Some of the most common challenges we hear about from customers are things that might be all too familiar to some of you. Things in IT have always changed rapidly, and it’s only picking up speed. The explosion of DevOps, cloud-centric architectures, and software-defined networking are making it increasingly difficult to keep monitoring and management tools in sync with the environment. This leads to another issue – management and individual teams lack visibility into the whole environment.