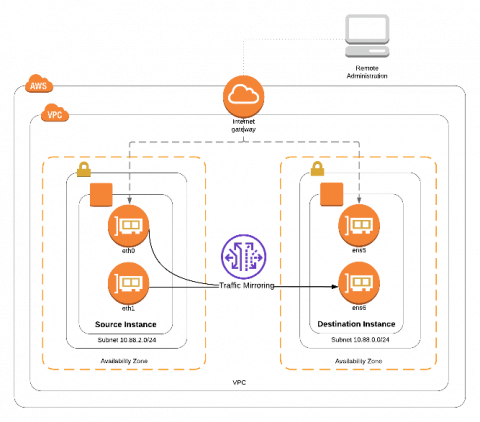
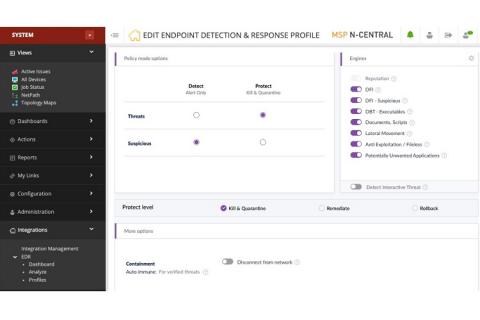
Make sure your Web servers support modern security protocols
To make sure no site content is modified or intercepted en route, HTTPS protocol is used (this is currently a must; using HTTP, insecure version, is strongly discouraged). Different versions of so called “transport security layer” protocol, known as TLS, can be used to provide the mentioned secure data exchange.