Operations | Monitoring | ITSM | DevOps | Cloud
Networks
The latest News and Information on IT Networks and related technologies.
3 MSP Sales Mistakes
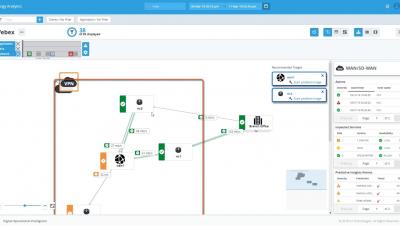
Context is Key: Additive vs. Subtractive Topology
Understanding the context of an IT incident can greatly reduce the MTTR and enhance the ability to determine the root cause. In an IT environment, ‘context’ is used to refer to the subset of information necessary to troubleshoot and diagnose an incident, or event. For some scenarios, the context may be the downstream dependencies after a high availability pair of firewalls goes offline, and in others, it may be the datastore in contention from multiple VMs.
To VPC or not to VPC? Pros and Cons in AWS Lambda
When you’re working with EC2 or containers, VPCs have long been viewed as a must-have. Without them, you will face a constant barrage of attacks aimed at your infrastructure and OS, such as brute force login attacks. But are VPCs still needed when it comes to AWS Lambda? What do you actually get when you put a function inside a VPC? And what are the downsides?
Understanding Istio Ingress
Istio is a hot technology right now. Giants such as Google and IBM have devoted entire teams of engineers to the project to push it to production readiness. Since 1.0 has been released recently, I wanted to write down some of the things that confused me coming from a strictly Kubernetes only world where we have Ingress controllers and Service load balancers and how Istio takes these same concepts but on stimulants.
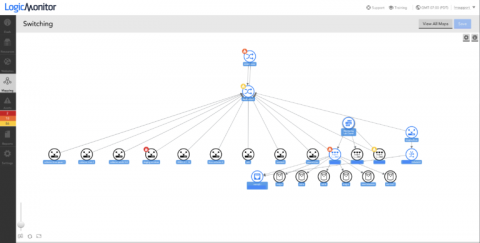
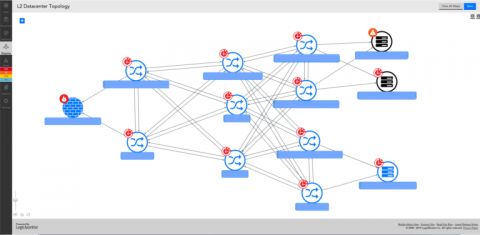
An Introduction to Dynamic Topology with LogicMonitor
LogicMonitor’s topology mapping functionality provides users with a scalable mapping solution that operates on an additive approach for establishing topological context (this means we only show what is necessary for your current viewing purposes).
IPAM. What is it? The major breakthrough of Pandora FMS Release 731
Today we will take a tour of the most technical Pandora FMS. For some people, it can be a challenge. Although the IPAM extension already existed in Pandora FMS world, in release 731 this extension was improved to the point of being considered as a new extension. But what is IPAM? What is IPAM? and what is it for?…. In this article we will answer these important questions to be able to use it.
Next Time You Configure or Update Your Network Interfaces Use This Checklist
ManageEngine wins at Future Network Awards-for the third time!
ManageEngine has added another gem to its crown, winning the Future Network Awards’ “Network Management and Monitor Vendor of the Year” award for the third time.
Comparing kube-proxy modes: iptables or IPVS?
kube-proxy is a key component of any Kubernetes deployment. Its role is to load-balance traffic that is destined for services (via cluster IPs and node ports) to the correct backend pods. Kube-proxy can run in one of three modes, each implemented with different data plane technologies: userspace, iptables, or IPVS. The userspace mode is very old, slow, and definitely not recommended! But how should you weigh up whether to go with iptables or IPVS mode?