Operations | Monitoring | ITSM | DevOps | Cloud
Networks
The latest News and Information on IT Networks and related technologies.
Deep Packet Inspection: What's next?
Since all technology traffic analysers have evolved, and in order to answer the question of what the next step in this evolution is many experts suggest that the deep packet inspection is the point to which all will evolve. However, deep packet inspection is not a new concept; ISPs have been using it, not without controversy, for some years. Then why is it referred to as the next step?
ipMonitor® Free Edition: Essential IT Monitoring
How to monitor Cisco ACI in Network Performance Monitor
How to monitor networks for dummies. Here is what you need
Ok, so you own a company, now what? All right, then one of the million things to keep in mind, in addition to the plant that you are going to buy for your office, is learning how to monitor networks. Think that if your computerized network stops working properly (for any reason) and the data that normally flows through it does not, the company is not functional anymore, during the whole time the disaster lasts.
How to Configure a Multicast Linux Network
In a world where consumer-level computing technology has been largely dominated by Windows, many users remain unaware of the need for administrators to configure and maintain network hardware and environments based on the Linux operating system. But Linux in its various distributions and the Unix operating system from which they derive have for decades provided the backbone for the core systems that make consumer-level computing and indeed many aspects of daily life possible.
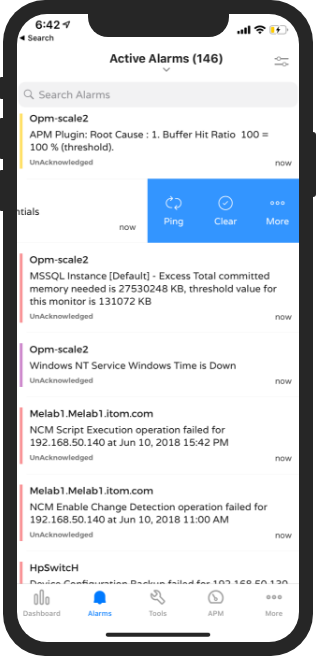
Become an eagle-eyed network admin using OpManager's push notifications
The secret to exceptional network management is periodically identifying and diagnosing network problems. Putting your experts at the network operations center (NOC) all day watching for a device to go down isn’t the best use of your workforce’s time. There has to be a smarter way to view potential network pitfalls without being glued to the chair in your NOC.
Zero Trust Security: Supporting a CARTA approach with Network Security
Setting Up Your First Client in Auvik
Traffic Analyzers: I already have a capture, and now what?
When we are faced with a performance problem related to those responsible for the applications and those responsible for the network platform, we usually think about how useful it would be to have a traffic analyzer that clarifies the real origin of the problem. Now, many times we see network analysts who after installing the tool feel overwhelmed by the amount of information it offers them.