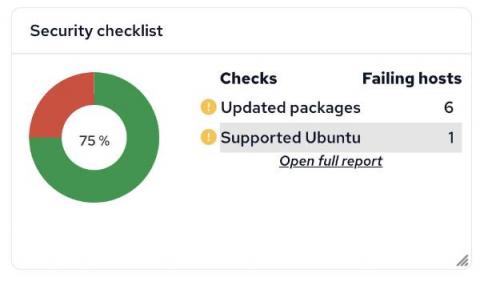
What Is Antivirus Software?
Antivirus software refers to any program that’s specially designed to detect and remove malicious software (malware). After installation, antivirus software usually works continuously in the background to offer real-time protection against viruses and malware. A comprehensive AV solution can help you protect your device or network from various cyberthreats like malware, spyware and phishing.