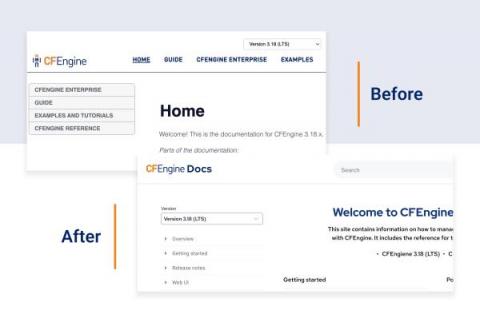
How to Automate Intune Device Reports with Torq
Whether for managing remote teams, supporting ‘bring your own device’ (BYOD) policies, or simply another layer in a data protection strategy, services like Microsoft Intune offer greater control over the devices on your network. But using the data from these services often requires tedious prep work, and this process is likely repeated multiple times a week, if not daily. Tedious, repetitive, structured: these are all signs that a process can and should be automated.