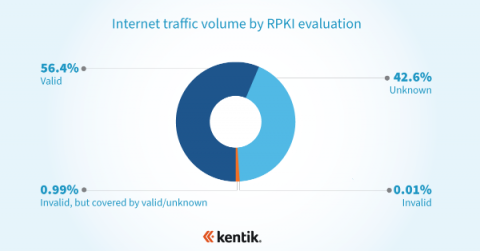
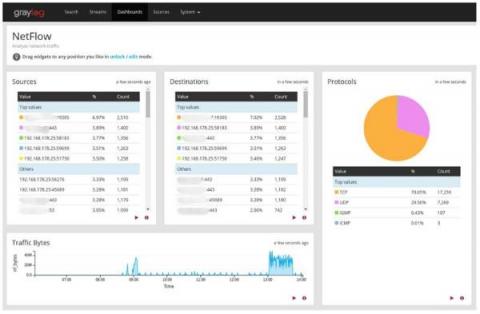
Automated Threat Hunting: A Closer Look
Proactively finding and eliminating advanced threats through threat hunting is a growing necessity for many organizations, yet few have enough resources or skilled employees to do it effectively. For those who do have an active threat hunting program, the process is often manual and time consuming. With cloud security automation, however, you can implement rules that automatically adjust your security policies based on the latest threat data.