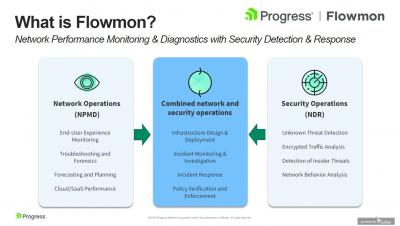
Two-factor authentication in Pandora FMS
I have been a regular user of Pandora FMS for years and the best I can say about them is that they always have something new to add to my learning. Today, for example, I rediscovered the Two-Factor authentication in Pandora FMS! *And I did it, in part, through this article already published on their blog Although I devote myself to programming (and it is what I like to do the most), I am more of a Web 2.0 person than a Web 3.0 person because I consider that the latter has been abused too much.