Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
CFEngine: The Agent Is In 11 - Infrastructure Hardening With CFEngine & Lynis
What is Red Teaming in Cyber Security? The Complete Guide
Red teaming is the practice of asking a trusted group of individuals to launch an attack on your software or your organization so that you can test how your defenses will hold up in a real-world situation. Any organization reliant on software – including banks, healthcare providers, government institutions, or logistics companies – is potentially vulnerable to cyberattacks, such as ransomware or data exfiltration.
Automated Just-In-Time Permissions Using JumpCloud+Torq
For security teams, properly managing which users can access resources and governing the level of access those users have is about as basic as locking the door at night. Understandably then, there are thousands of options available to fine-tune or revoke access, and it’s likely that issues come up daily for most companies—if not hourly.
Trigger arbitrary code from PostgreSQL
In this blog post we show how it is possible to run an arbitrary program, script, or execute arbitrary code in reaction to changes and generally events in a PostgreSQL database.
Building Your Security Analytics Use Cases
It’s time again for another meeting with senior leadership. You know that they will ask you the hard questions, like “how do you know that your detection and response times are ‘good enough’?” You think you’re doing a good job securing the organization. You haven’t had a security incident yet. At the same time, you also know that you have no way to prove your approach to security is working. You’re reading your threat intelligence feeds.
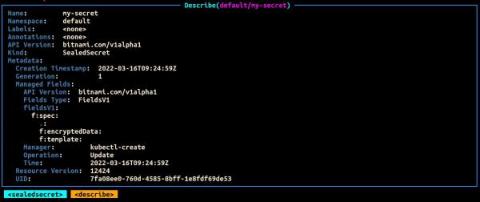
Managing Sensitive Data in Kubernetes with Sealed Secrets and External Secrets Operator (ESO)
Having multiple environments that can be dynamically configured has become akin to modern software development. This is especially true in an enterprise context where the software release cycles typically consist of separate compute environments like dev, stage and production. These environments are usually distinguished by data that drives the specific behavior of the application.
Elastic on Elastic - Using Elastic Observability to optimize the performance of detection rules in Elastic Security
Elastic Security’s developer support team has recently seen a surge in reports from customers about sluggish performance in our UI. Our initial inspection of logs for troubleshooting provided some insights, but not enough for a true fix. Luckily, we have Elastic Observability and its APM capabilities to dive in deeper and look under the hood at what was really happening within Elastic Security. And, more importantly, how we could improve its performance for customers.
VMware Tanzu Community Edition Taps in Cartographer for Building Secure Adaptable Cloud Native Supply Chains
The latest update to the VMware Tanzu Community Edition further streamlines the path to production with the addition of Cartographer, an open source project to build and manage modern secure software supply chains.