Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
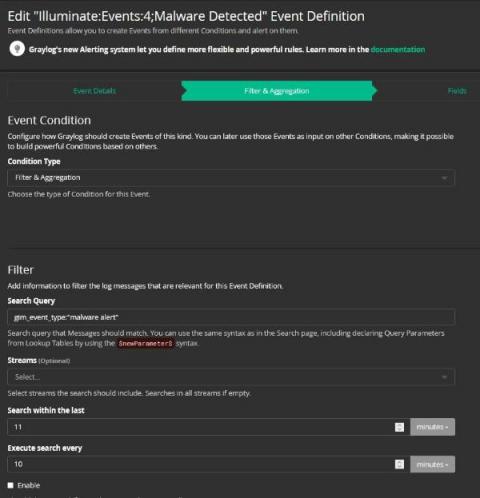
Elastic on Elastic - Using Elastic Observability to optimize the performance of detection rules in Elastic Security
Elastic Security’s developer support team has recently seen a surge in reports from customers about sluggish performance in our UI. Our initial inspection of logs for troubleshooting provided some insights, but not enough for a true fix. Luckily, we have Elastic Observability and its APM capabilities to dive in deeper and look under the hood at what was really happening within Elastic Security. And, more importantly, how we could improve its performance for customers.
Open source security coverage and compliance with Ubuntu Pro on public clouds
For businesses utilising public clouds, choosing an open source platform offers considerable advantages. Open source solutions can help reduce costs, provide access to the most leading-edge enterprise-grade features, and eliminate risks such as vendor lock-in, lack of support, or long-term security maintenance.
Change in behavior: Directory permissions and the execute bit
rxdirs has provided a convenient default when setting permissions recursively. When enabled (the default prior to version 3.20.0) a promise to grant read access on a directory is extended to also include execution since quite commonly if you want to read a directory you also want to be able to list the files in the directory. However, the convenience comes with the cost of complicating security reviews since the state requested on the surface is more strict than what is actually granted.
Getting started with CFEngine Pt. 1.5 - Local installation with vagrant
Cybersecurity Risk Management: Introduction to Security Analytics
It’s mid-morning. You’re scanning the daily news while enjoying a coffee break. You come across yet another headline broadcasting a supply chain data breach. Your heart skips a quick, almost undetectable, beat. You have the technology in the headline in your stack. You set aside your coffee and begin furiously scanning through the overwhelming number of alerts triggered across all your technologies.
Splunk Indexer Vulnerability: What You Need to Know
A new vulnerability, CVE-2021-342 has been discovered in the Splunk indexer component, which is a commonly utilized part of the Splunk Enterprise suite. We’re going to explain the affected components, the severity of the vulnerability, mitigations you can put in place, and long-term considerations you may wish to make when using Splunk.
Get Back to the Basics for World Backup Day 2022
In recent weeks, international headlines have been dominated by the Russia-Ukraine war and its potential to escalate into cyberspace due to punishing economic sanctions by the west. On March 21st, 2022, the Biden administration released a statement calling for the public and private sector to “accelerate efforts to lock their digital doors” in light of the Russian cyber threat.
Why ZTNA Solutions are Important Right Now
2021 marked the fifth consecutive year of record-breaking security attacks. Zero-Day attacks skyrocketed, with 66 exploits found to be in use, more than any other year on record and almost double 2020’s figure. Meanwhile, a staggering 66% of organizations have suffered at least one ransomware attack in the last year, with the average ransom payment soaring by 63% to $1.79 million (USD).
Top 3 Reasons Why You Should Work with a ZTNA Service Partner
With remote and hybrid working now commonplace for organizations, many IT departments are weighing up the pros and cons of moving to a Zero Trust Network Access (ZTNA) model to replace traditional VPN, or other remote access approaches. While the benefits of moving to ZTNA are compelling: improving user experience, providing enhanced security, reducing management overhead, and increasing visibility and control, it can often be a challenge to select the best approach for your business.