Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Cloud SIEM: Modernize Security Operations and your Cyber Defense
Customer Highlight: HIPAA Vault
As an MSSP (Managed Security Service Provider), HIPAA Vault relies on CFEngine to automate & secure their infrastructure on behalf of their customers. HIPAA Vault has been a longtime CFEngine Community user since 2012 and recently upgraded to Enterprise in order to boost their infrastructure visibility through Mission Portal and features like Compliance Reporting that help them provide a more secure & compliant cloud hosting solution.
Automated Patch Management and Team Swarming are Key Security Practices
In the blink of an eye, you can miss a new business disrupting security incident. We all recognize that cybersecurity breaches are increasing in volume and sophistication. How we respond to them is critical. Security vulnerabilities force organizations to go outside of their daily activities to execute out-of-band responses. We face numerous challenges in managing security risk.
Detecting rare and unusual processes with Elastic machine learning
In SecOps, knowing which host processes are normally executed and which are rarely seen helps cut through the noise to quickly locate potential problems or security threats. By focusing attention on rare anomalies, security teams can be more efficient when trying to detect or hunt for potential threats. Finding a process that doesn’t often run on a server can sometimes indicate innocuous activity or could be an indication of something more alarming.
Automating key rotation for CI/CD pipelines
With the new Contexts API release, developers can save their team valuable time while enhancing security practices. We know maintaining your organization’s security is crucial. There is the need to meet strict compliance guidelines, such as FedRAMP and GDPR, and what seems to be an increasing number of breaches, like the compromise of over 150,000 video security cameras as a result of a targeted Jenkins server.
It's Never Too Late to Improve Your Personal Security Posture
Analytics-Based Investigation and Automated Response with AWS + Splunk Security Solutions
Organizations are migrating an increasing amount of their infrastructure into the cloud. The cloud provides organizations with a number of benefits like greater scalability, improved reliability and faster time to value. However, these potential benefits can be offset if security is an afterthought.
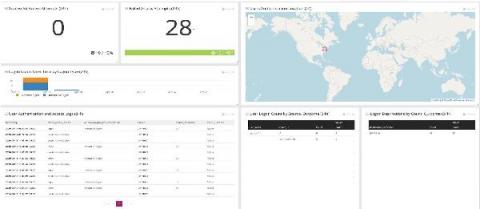
Monitoring Logs for Insider Threats During Turbulent Times
For logs and tracking insider threats, you need to start with the relevant data. In these turbulent times, IT teams leverage centralized log management solutions for making decisions. As the challenges change, the way you’re monitoring logs for insider threats needs to change too. Furloughs, workforce reductions, and business practice changes as part of the COVID stay-at-home mandates impacted IT teams.
Unraveling open port threats and enhancing security with port scanning tools
From exposing your network vulnerabilities to becoming a passageway for intruders, open ports can pose several risk vectors that threaten your network’s confidentiality, integrity, and availability. This is why it’s a best practice to close your open ports. To tackle the risks introduced by open ports, network admins rely on port scanning tools to identify, inspect, analyze, and close open ports in their networks.