Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Industry-First Pay-as-you-go SaaS Platform for Kubernetes Security and Observability
We are excited to introduce Calico Cloud, a pay-as-you-go SaaS platform for Kubernetes security and observability. With Calico Cloud, users only pay for services consumed and are billed monthly, getting immediate value without upfront investment.
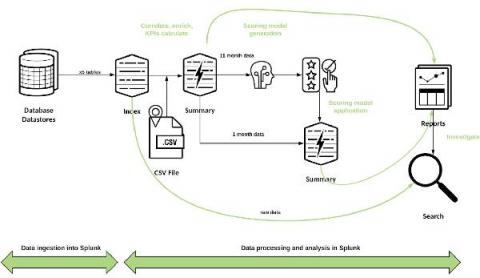
Creating a Fraud Risk Scoring Model Leveraging Data Pipelines and Machine Learning with Splunk
According to the Association of Certified Fraud Examiners, the money lost by businesses to fraudsters amounts to over $3.5 trillion each year. The ACFE's 2016 Report to the Nations on Occupational Fraud and Abuse states that proactive data monitoring and analysis is among the most effective anti-fraud controls.
Bullet-Proofing Serverless Infrastructures with Failure and Threat Detection
When building cloud-based systems and serverless systems, in particular, it’s crucial to stay on top of things. Your infrastructure will be miles away from you and not a device you hold in your hands like when you build a frontend. That’s why adding a monitoring solution to your stack, which offers a pre-configured serverless failure detection, should be one of the first decisions.
Reducing Supply Chain Attack Surface through SaaS
We’ve all been watching closely as the Solarwinds hack, known as SUNBURST, gets its due analysis. This attack was sophisticated and rightfully should concern any company. Companies are now — or should be — considering not only what products they are using but to what attack vectors those products are exposed that unduly extend attack surfaces. Solarwinds makes great products — I’ve used them for years.
cf-remote is now available via pip
cf-remote is a tool for downloading and installing/deploying CFEngine. It automates a lot of the things you have to do before CFEngine is actually installed on your infrastructure, such as provisioning cloud instances, downloading CFEngine installers, copying them to remote hosts and installing / bootstrapping. To make it as easy as possible to get started with cf-remote and CFEngine, it is now available on pypi.
Security vs. Compliance: What's the difference?
The first two posts in our compliance blog series focused on managing compliance through automation. In this third post, we take a step back to explore a more foundational — but no less important — topic: What’s the difference between compliance and security? Is compliant infrastructure secure infrastructure? People often talk about compliance and security as though they’re one and the same.
Using GitHub Actions to publish releases to pip/pypi (Developer demo)
Not All Buzzwords are Created Equal: Real Applications of Zero Trust Security for IoT
Zero Trust security. Some would say it’s the latest and greatest buzzword and this disposition is understandable given the amount of jargon introduced into the Information Technology market each year. With vernacular being used interchangeably like “AI,” “Machine Learning,” and “Deep Learning,” these words get stripped of their real significance.
Show your Website some Love this Valentine's Day
If you care about your website, show it some love this Valentine’s Day. RapidSpike is there, like Fred from First Dates, to keep the spark alive. We will be your relationship counsellor through the tough times with your website, from downtime to Magecart style attacks, and even the occasional website launch! They say healthy relationships are built around the pillars of trust, communication and passion.