Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Using Ivanti Neurons and MobileIron UEM to Handle the Latest iOS, iPadOS, and tvOS Vulnerabilities Proactively
On Tuesday, January 26, 2021, Apple released version 14.4 of its iOS, iPadOS, and tvOS products that included patches for three security vulnerabilities that affect iPhone 6s and later, iPad Air 2 and later, iPad mini 4 and later, and iPod touch 7th generation, as well as Apple TV.
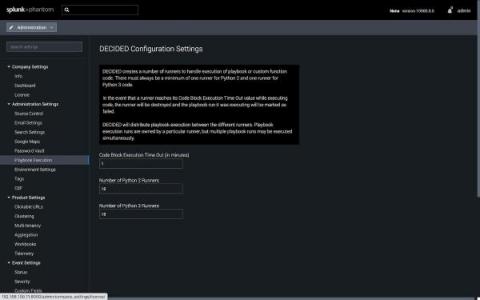
Next Level Automation: What's New with Splunk Phantom
Splunk Phantom 4.10 introduced many new enhancements, including the ability to develop playbooks in Python 3. In fact, Python 3 is now the default for Splunk Phantom playbooks. In doing so, we needed to create two different “playbook runners” to ensure we could continue to support playbooks written in Python 2.7 while also supporting Python 3.
Detecting MITRE ATT&CK: Defense evasion techniques with Falco
The defense evasion category inside MITRE ATT&CK covers several techniques an attacker can use to avoid getting caught. Familiarizing yourself with these techniques will help secure your infrastructure. MITRE ATT&CK is a comprehensive knowledge base that analyzes all of the tactics, techniques, and procedures (TTPs) that advanced threat actors could possibly use in their attacks. Rather than a compliance standard, it is a framework that serves as a foundation for threat models and methodologies.
Security risks of monitoring services: Why to always use a read-only solution
In the mid of December, SolarWinds disclosed that the company experienced a highly sophisticated, manual supply chain attack on versions of the Orion network monitoring product released in March – June 2020. The company shared that the attack was most likely conducted by foreign hackers and intended to be narrow, remarkably targeted, and manually executed attack.
Securing SQL Server with DoD STIGs
Elastic is going closed-source. Where does that leave MSSPs?
Elastic moved from an open source license for Elasticsearch and Kibana to a “source available” (aka closed source) license. It was supposed to shut down SaaS companies, but what does it mean for Managed Security Service Providers? Managed Security Service Providers, or MSSPs, are a growing segment in the security business. These firms specialize in deploying security infrastructure, aggregating monitoring and event data, and proactively hunting threats.
Introducing GitHub Discussions for CFEngine
We are excited to announce that CFEngine is now using GitHub Discussions. GitHub Discussions is a feature of GitHub repos, and similar to Q&A platforms like Stack Overflow, and other online forums. After testing it out for a few weeks we are pleased with how it works and want to encourage all our users to try it.