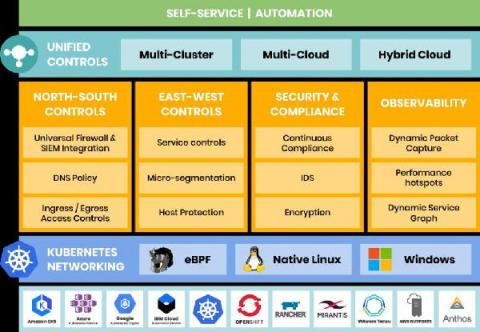
Why Use Active Directory Security to Improve Your Server Security?
How do you secure your network servers, laptops, desktops, and workstations? A good starting point is to have a checklist of how to enable security features on these devices. You also need to enable a server monitoring service to track specific events and generate event logs. Yet, your security tasks are never done. You can get a false sense of security if you merely go through your checklist of security items and stop.