Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Detecting the Sudo Baron Samedit Vulnerability and Attack
On January 26th, 2021, Qualys reported that many versions of SUDO (1.8.2 to 1.8.31p2 and 1.9.0 to 1.9.5p1) are vulnerable (CVE-2021-3156) to a buffer overflow attack dubbed Baron Samedit that can result in privilege escalations. Qualys was able to use this vulnerability to gain root on at least Ubuntu 20.04 (Sudo 1.8.31), Debian 10 (Sudo 1.8.27), and Fedora 33 (Sudo 1.9.2), some of the most modern and widely used Linux operating systems.
7 Ways GroundWork Delivers Bulletproof Infrastructure Monitoring
Lately, security has become top of mind across infrastructure monitoring customers. This is no surprise considering the widespread reports about supply-chain vulnerabilities and embedded compromises rampant in popular network monitoring software. In light of this, we want to underscore how seriously we have always taken our security processes, and how we cultivate a culture based on a foundation of sound security protocols.
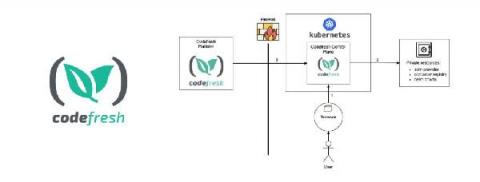
What Is Zero Trust & How Do We Implement It to Run Secure CI/CD Workflows in Kubernetes?
Zero trust is a security concept that is centered around the idea that organizations should never trust anyone or anything that does not originate from their domains. Organizations seeking zero trust automatically assume that any external services it commissions have security breaches and may leak sensitive information.
Datadog achieves FedRAMP Moderate Impact authorization
As government agencies accelerate migrating their operations to the cloud, they need to adhere to strict compliance and security standards. The Federal Risk and Authorization Management Program (FedRAMP) provides the standard that these agencies—and their private-sector partners—must meet to work and manage federal data safely in the cloud.
What's new in Sysdig - January 2021
Welcome to another monthly update on what’s new from Sysdig. Our team continues to work hard to bring great new features to all of our customers, automatically and for free!
Learn how to comply now before your next audit
Are you struggling to keep up with manual compliance across your infrastructure? In this 25-minute episode of the Pulling the Strings podcast, powered by Puppet, learn how Puppet Comply makes automating your configuration compliance easy -- with full view dashboards and the ability to assess, remediate and enforce all through the Puppet Enterprise solution. Listen in and discover:
How to set AWS S3 Bucket Read Permissions with Relay
Cloud environments are susceptible to security issues. A big contributor is misconfigured resources. Misconfigured S3 buckets are one example of a security risk that could expose your organization’s sensitive data to bad actors. Policies and regular enforcement of best practices are key to reducing this security risk. However, manually checking and enforcing security is time-consuming and can fall behind with all the demands a busy DevOps team faces every day.
How to export and import Timelines and templates from Elastic Security
When performing critical security investigations and threat hunts using Elastic Security, the Timeline feature is always by your side as a workspace for investigations and threat hunting. Drilling down into an event is as simple as dragging and dropping to create the query you need to investigate an alert or event.