Fail2ban Monitoring with InfluxDB and Telegraf
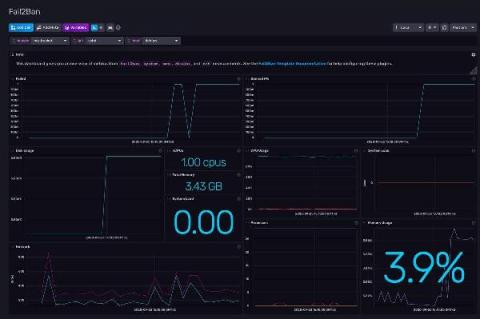
If you have a server open to the internet on Port 22 (the default port for SSH servers), it’s common to find several “Failed password” in your auth.log (log file) every minute, due to bots constantly browsing the internet for servers that are easy to hack with common passwords. But if your auth.log is growing very fast and SSH daemon randomly refuses to create new connections, then someone probably marked your server as a target for coordinated SSH brute-force attack.