Operations | Monitoring | ITSM | DevOps | Cloud
SIEM
Automatic correlation of FireEye red team tool countermeasure detections
Getting started with EventSentry v4.2.x
Building your modern cloud SIEM
Building your modern SIEM, Unique security requirements for cloud and modern technologies
Automation in Less than 7 Clicks!
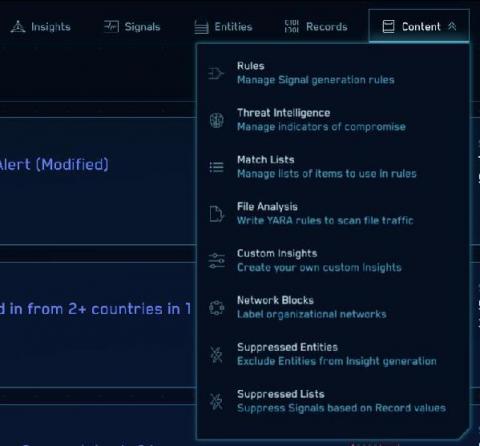
Highlight Critical Security Attacks with Logz.io's New Alerts Correlation
The ever-evolving cloud-native landscape creates constantly changing attack surfaces. As a result, teams implement a whole suite of security tools to identify large varieties of vulnerabilities and attacks, as well as monitor more logs than ever to find malicious activity. But monitoring so much information can cause a barrage of notifications and alerts. Even if you’re identifying real security threats, it can be impossible to know where to start and where to focus.
Shipping Sysmon Logs to Logz.io Cloud SIEM
System Monitor (Sysmon) is Windows’ service for monitoring activity and recording it to the Windows event log. It is the go-to for logging anything on a PC. Sysmon will immediately log events, capturing vital info. The driver for Sysmon will install as a boot-start driver, enabling capture of any and all events from the get-go. Now, you can send Sysmon logs straight to Logz.io Cloud SIEM.
SIEM Tutorial: What should a good SIEM Provider do for you?
Modern day Security Information and Event Management (SIEM) tooling enterprise security technology combine systems together for a comprehensive view of IT security. This can be tricky, so we’ve put together a simple SIEM tutorial to help you understand what a great SIEM provider will do for you. A SIEM’s responsibility is to collect, store, analyze, investigate and report on log and other data for incident response, forensics and regulatory compliance purposes.
Triaging Log Management Through SIEMS
While all cybersecurity professionals agree that log management is integral for robust proactive and reactive security, managing the enormous amount of data logs can be a challenge. While you might be tempted to collect all logs generated from your systems, software, network devices, and users, this “fear of missing out” on an important notification ultimately leads to so much noise that your security analysts and threat hunters cannot find the most important information.