Operations | Monitoring | ITSM | DevOps | Cloud
Flowmon
Network Detection & Response Optics
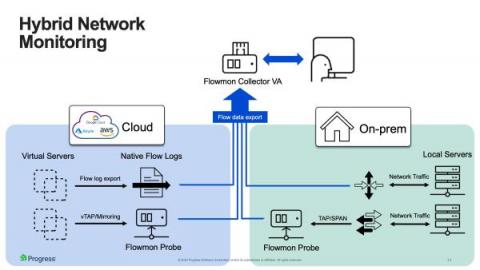
Hybrid Cloud Monitoring and Performance Management
Many organizations manage a hybrid infrastructure spread over on-premise and multiple public cloud platforms such as AWS, Azure and Google for specific business applications. The hybrid cloud approach has advantages but adds more complexity for IT teams responsible for keeping IT systems safe and secure. The monitoring tools system administrators use for on-premise infrastructure are often unsuitable for monitoring public cloud platforms.
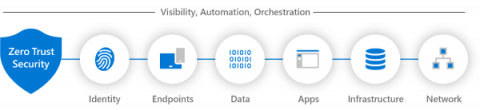
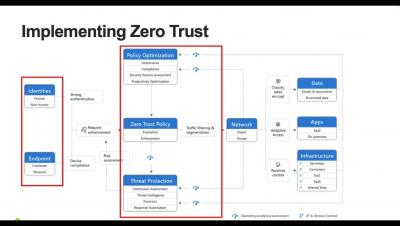
Applying Zero Trust to Data Centre Networks
Zero trust isn’t an approach that can be delivered by buying a single product that claims to provide it. Instead, it is an approach that needs to be understood and implemented in complementary ways across an organization’s IT systems. We recently hosted a webinar titled Applying Zero Trust to Data Centre Networks to provide guidance on how organizations can use zero trust to enhance the security of their IT systems. The webinar details are below, after a summary of the topics covered.
Multi-Cloud - Rise of Hybrid Networks and the Need to Monitor & Secure Them
This model has benefits, but at the same time, it introduces complexity for the IT teams tasked with monitoring and securing IT systems. Existing network monitoring technologies that system admins use with on-premise infrastructure are typically not expandable to include infrastructure and services running on public cloud platforms. This is a problem as you cannot manage and secure what you cannot see.
Flowmon Integrations into Enterprise Ecosystem
Flowmon is not a stand-alone system used in isolation. It is part of an ecosystem of monitoring and security tools used across the enterprise. Recently, we have introduced new integrations with Splunk and ServiceNow to simplify interoperability and enable IT and security teams to be more efficient. This is a good opportunity to remind of all the integration options and resources we have.