Operations | Monitoring | ITSM | DevOps | Cloud
Elastic
Search and replicate across regions and cloud service providers with Elastic Cloud
We are excited to announce the general availability of cross-cluster search and replication on Elastic Cloud. These two features allow you to search and replicate data across clusters in different regions and cloud service providers globally, making it possible to: Be sure to dive in and learn more about the features below! Cross-cluster search lets you search remote clusters across multiple regions and cloud service providers. When you break down regional data silos, you can get insights faster.
Deploying Elastic to further strengthen IT security at TierPoint
TierPoint is a leading provider of secure, connected data center and cloud solutions at the edge of the Internet with thousands of customers. At TierPoint, I’m responsible for maintenance and development of the information security program, which includes threat analytics, incident response, and digital forensics. We’re constantly looking for new and even more effective ways to aggregate, process, and make decisions from massive amounts of data streaming in from diverse sources.
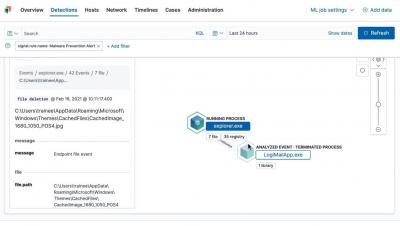
Detecting Cobalt Strike with memory signatures
At Elastic Security, we approach the challenge of threat detection with various methods. Traditionally, we have focused on machine learning models and behaviors. These two methods are powerful because they can detect never-before-seen malware. Historically, we’ve felt that signatures are too easily evaded, but we also recognize that ease of evasion is only one of many factors to consider.
Elastic named a Leader in the 2021 GigaOm Radar on Cloud Observability
We are thrilled that Elastic has been recognized as a Leader and a Fast Mover in the 2021 GigaOm Radar Report for Cloud Observability. GigaOm Radar reports offer a forward-looking view of the market and are designed to help IT decision makers evaluate solutions with an eye to the future. Their analysts consider not just where the solutions are today, but also how the market is evolving and where the solutions are headed relative to that trend.
Elastic Cloud Value Calculator: Understand the economics of adopting Elastic Cloud
As your Elastic usage increases and your use cases expand, it's important to know the benefits and cost savings that you can achieve by running Elasticsearch as a service. But since every Elasticsearch implementation can vary by use case and deployment model, it can be complicated to tackle on your own. So with that in mind, we are excited to share the Elastic Cloud Value Calculator.
Elastic Security 101
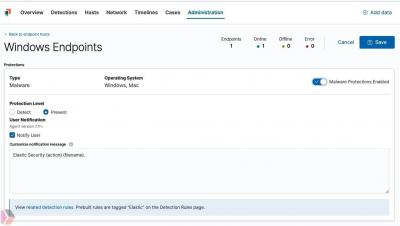
How to configure your Endpoint Integration policy in Elastic Security
Validating Elastic Common Schema (ECS) fields using Elastic Security detection rules
The Elastic Common Schema (ECS) provides an open, consistent model for structuring your data in the Elastic Stack. By normalizing data to a single common model, you can uniformly examine your data using interactive search, visualizations, and automated analysis. Elastic provides hundreds of integrations that are ECS-compliant out of the box, but ECS also allows you to normalize custom data sources. Normalizing a custom source can be an iterative and sometimes time-intensive process.