SolarWinds Server Configuration Monitor Overview
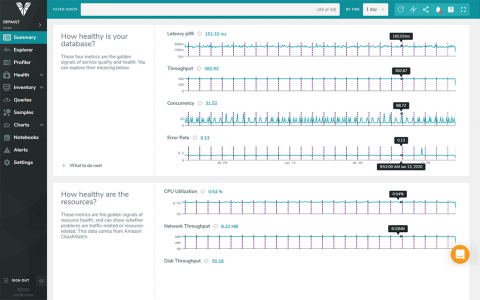
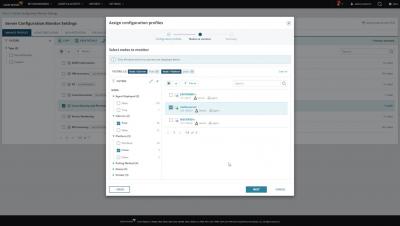
SolarWinds Server Configuration Monitor (SCM) is designed to provide insights into Windows® server and application changes to help you pinpoint the root cause of performance problems faster. Detect, track, and receive alerts when changes occur, allowing you to correlate system performance against configuration changes, know who made changes, and compare configurations over time. SCM integrates with SolarWinds Server & Application Monitor, allowing you to extend troubleshooting of system and application performance from one unified console.