Operations | Monitoring | ITSM | DevOps | Cloud
Compliance
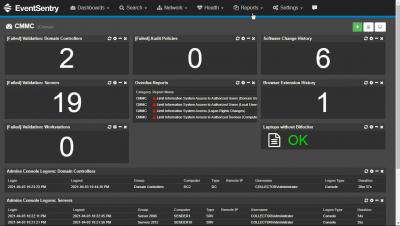
CMMC compliance with EventSentry
Automating STIG compliance and reporting
Applying the Roles and Profiles Method to Compliance Code
How to set up Software Security and Compliance for Your Artifacts
Applying the Roles and Profiles Method to Compliance Code
Most of you are familiar with the roles and profiles method of writing and classifying Puppet code. However, the roles and profiles method doesn’t have to exist only in your control repository. In fact, as I’ve been developing Puppet code centered around compliance, I’ve found that adapting the roles and profiles method into a design pattern to Puppet modules makes the code more auditable, reusable, and maintainable!
Security vs. Compliance: What's the difference?
The first two posts in our compliance blog series focused on managing compliance through automation. In this third post, we take a step back to explore a more foundational — but no less important — topic: What’s the difference between compliance and security? Is compliant infrastructure secure infrastructure? People often talk about compliance and security as though they’re one and the same.
Managing Compliance Drift: Break the endless scan-fix-drift cycle
In the first post of this series, we provided guidance for managing the many facets of a compliance program — taming the “compliance beast.” While there are many factors to consider, I’d argue that none is more essential than a reliable means of enforcement.
Datadog achieves FedRAMP Moderate Impact authorization
As government agencies accelerate migrating their operations to the cloud, they need to adhere to strict compliance and security standards. The Federal Risk and Authorization Management Program (FedRAMP) provides the standard that these agencies—and their private-sector partners—must meet to work and manage federal data safely in the cloud.
Learn how to comply now before your next audit
Are you struggling to keep up with manual compliance across your infrastructure? In this 25-minute episode of the Pulling the Strings podcast, powered by Puppet, learn how Puppet Comply makes automating your configuration compliance easy -- with full view dashboards and the ability to assess, remediate and enforce all through the Puppet Enterprise solution. Listen in and discover: