Operations | Monitoring | ITSM | DevOps | Cloud
IoT
Selecting Your Next Project's MCU
Selecting the best chip can be tedious work but the best chip can save you a lot of time and money, and might even be faster! So should you spend time finding the best? I have some words on the topic. If a primary goal of your next project is to learn a new MCU, you want to create something easily reproducible, or if there will be only one machine building the project, then I recommend you to go with the chip you want to learn, the chip most readily available, or the easiest one to work with.
Don't let the skills gap hinder your IoT success
Since the term Internet of Things (IoT) was first coined in 1999, the market has experienced vast growth and maturity, evolving rapidly – and it is showing no sign of slowing down. According to Omdia, the number of global satellite IoT connections is set to continue growing at a compound annual growth rate of 25% for the foreseeable future.
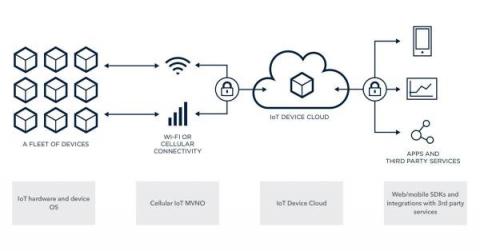
Top Things To Consider When Connecting IoT Devices To The Cloud
Particle's Fleet Health Feature, Powered by InfluxDB, Delivers Device-Specific Data for IoT Deployments
The Particle platform enables companies to manage and program their IoT devices, bringing them to market quicker. To accomplish this, Particle developers needed to be able to collect telemetry data from a large number of edge IoT devices to measure performance. A key benefit of the Particle platform is its ability to scale from prototype to enterprise. Developers often prototype IoT devices using microcontrollers like Arduino or Raspberry Pi.
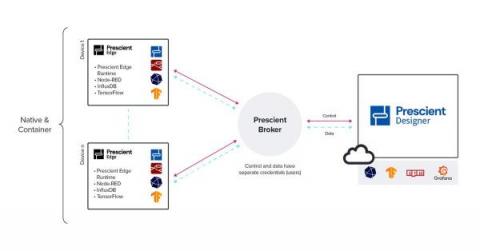
Prescient Devices Makes Managing IoT Edge Devices Easy with InfluxDB
Prescient Devices focuses on changing the way businesses think about and use edge data and industrial IoT. The company built Prescient Designer, an edge data solutions platform that gives organizations the boost they need to transform their IT/OT processes. Prescient’s products empower data engineers, system integrators, and innovators to easily design and orchestrate edge-to-cloud data solutions.
Using MQTT and InfluxDB for IoT
IoT Developer Technical Skills You Should Master to Build a Career
Introduction to Ubuntu Core 20
What Should I Know About Defending IoT Attack Surfaces?
The Internet of Things needs to be part of the overall corporate information security policy to prevent adversaries from using these devices as an entry point. There are several reasons why it’s critical for organizations to defend their IoT attack surface, most importantly being that IoT devices are powerful systems containing compute, storage, and networking that threat actors view as the easiest way to breach an organization or enable exploits.