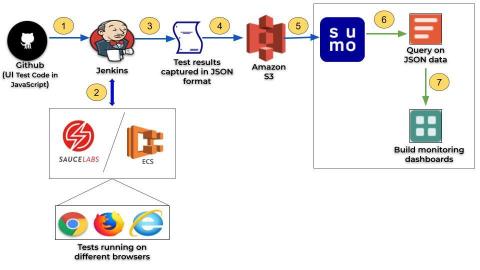
Glitch List: April 2019
Glitches happen. Even to the best of us. And rather than promote others’ misfortune, we created this list to highlight the importance of anomaly detection – and as a warning against denial. Because if it can happen to the world’s most-recognized companies, it can certainly happen to you.