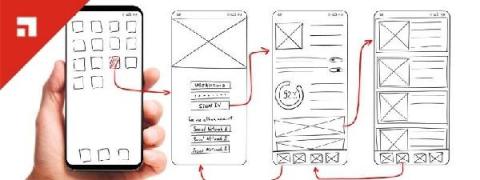
To Accelerate or Not to Accelerate, That is the Question: Software Updates and iOS 14.4
On Tuesday, January 26, 2021, Apple released iOS and iPadOS 14.4. As with previous releases, each new OS update is available to all Apple devices capable of running iOS and iPadOS 14. If you’re an IT admin, you should evaluate how you want to approach the latest release. Do you want to accelerate or slow down the updates? One concern we often hear about is that the apps that a company is deploying may not be compatible or may not have been tested with the latest release.