Simplifying security auditing, Part 2: Auditing systems that store sensitive data
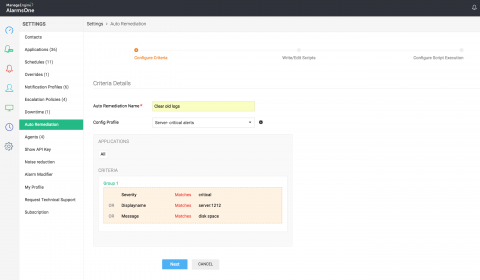
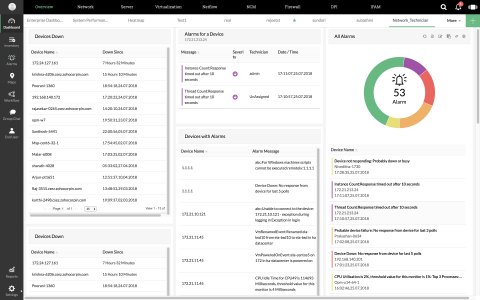
In part 1, we looked at an overview of auditing servers. In this blog, we’ll discuss which events you need to audit in your databases and file servers where sensitive data is stored. New data protection regulations and large-scale global attacks have made this more important than ever before. The main goal is to not only ensure that the accesses and modifications to sensitive data in your network are authorized, but also that file and column integrity are maintained.