Continuous Data: The Complete Guide
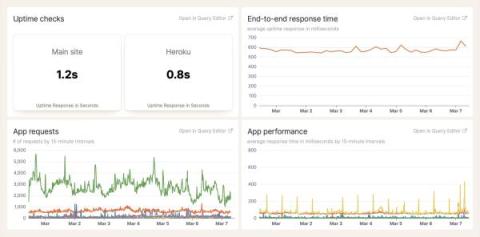
Data is never just data. There are structured and unstructured data, qualitative and quantitative data. Among these varied types, continuous data stands out as a key player, especially in the quantitative realm. Continuous data, with its infinite possibilities and precision, captures the fluidity of the real world — from the microseconds of a website’s load time to the fluctuating bandwidth usage on a network.