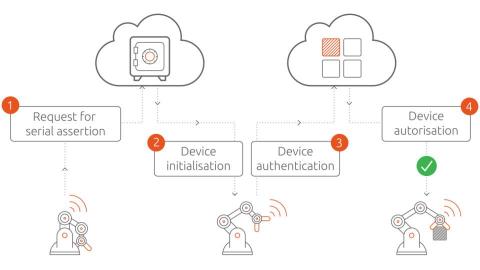
Visualizing Kubernetes scheduling and infrastructure scaling constraints
Every application has its unique compute infrastructure requirements. This is why container orchestrators such as Kubernetes provide application engineers with the use of taints and affinities to control precisely where pods run.