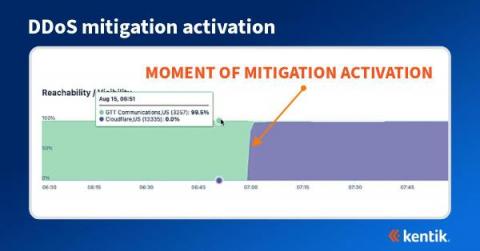
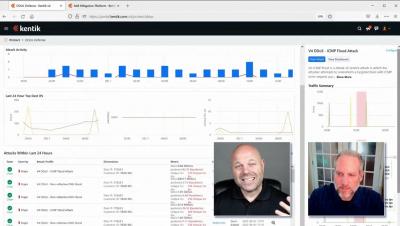
How BGP propagation affects DDoS mitigation
We often think of DDoS attacks as volumetric malicious traffic targeted against organizations that effectively take a service offline. Most frequently detected by anomalous behavior found in NetFlow, sFlow, IPFIX, and BGP data, what may not be well understood is how the DDoS mitigation works and how it’s possible to visualize the effectiveness of the mitigation during and after an attack.