Operations | Monitoring | ITSM | DevOps | Cloud
SIEM
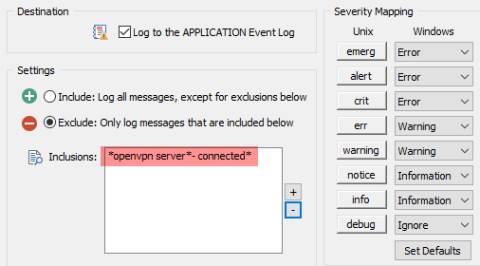
EventSentry Troubleshooting: Managing Database Size
EventSentry Troubleshooting: Reducing the number of email notifications
5 Best SIEM Tools and How to Choose
Predict the Future! A universal approach to detecting malicious PowerShell activity
So, here’s the deal with AntiVirus software these days: It’s mostly playing catch-up with super-fast athletes — the malware guys. Traditional AV software is like old-school detectives who need a picture (or, in this case, a ‘signature’) of the bad guys to know who they’re chasing. The trouble is, these malware creators are quite sneaky — constantly changing their look and creating new disguises faster than AntiVirus can keep up with their photos.
Sending Data to Elastic Security With Cribl Stream (And Making It Work With Elastic SIEM)
Cribl Stream is a real-time security and observability data processing pipeline that can be used to collect, transform, enrich, reduce, redact, and route data from a variety of sources to a variety of destinations. One of the popular destinations for Cribl users is Elastic SIEM. This blog post will walk you through the steps on how to set up Cribl Stream to normalize and forward data to use with Elastic Security for SIEM.
SIEM Implementation Guide: A How-To Guide
In an era where cybersecurity threats are not just frequent but increasingly sophisticated (and becoming more costly), the need for robust defense mechanisms has never been more critical. Security Information and Event Management (SIEM) emerges as a cornerstone in this complex data environment. It’s not just another tool in your cybersecurity toolkit; it’s a solution designed to elevate your organization’s security posture.
Modernize Your SIEM Architecture
In this Livestream conversation, I spoke with John Alves from CyberOne Security about the struggles teams face in modernizing a SIEM, controlling costs, and extracting optimal value from their systems. We delve into the issues around single system-of-analysis solutions that attempt to solve detection and analytics use cases within the same tool.
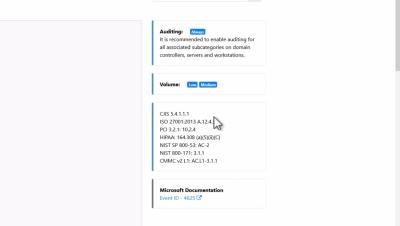
CMMC v2 Compliance with EventSentry
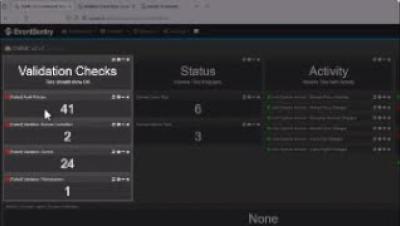
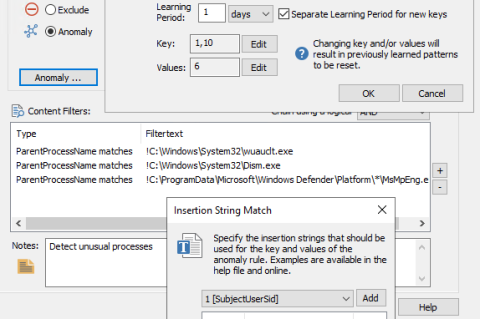
EventSentry v5.1: Anomaly Detection / Permission Inventory / Training Courses & More!
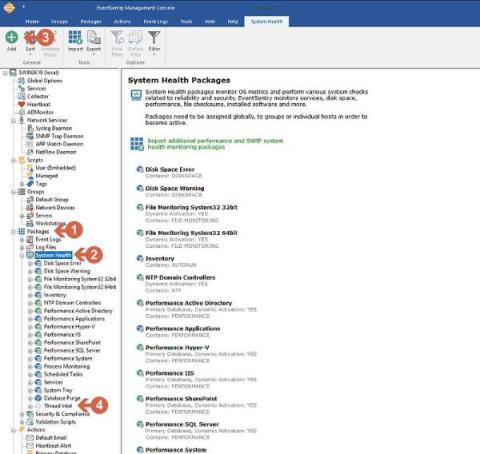
We’re extremely excited to announce the availability of the EventSentry v5.1, which will detect threats and suspicious behavior more effectively – while also providing users with additional reports and dashboards for CMMC and TISAX compliance. The usability of EventSentry was also improved across the board, making it easier to use, manage and maintain EventSentry on a day-by-day basis. We also released 60+ training videos to help you get started and take EventSentry to the next level.