Operations | Monitoring | ITSM | DevOps | Cloud
Latest Posts
How to Quickly Find What's Broken in Your Complex, Cloud Environment
How To Get Complete Visibility of Your Services
Software Development Life Cycle: Day 1 Best Practices
Introducing Three Powerful Commands in Cribl Search: .show objects, .show queries, and .cancel
Empty spaces, what are we searching for? Abandon queries, but do you know the score? On and on, Does anybody know what we are looking for? … Inspired by “The Show Must Go On”, Queen. Since we launched Cribl Search back in late 2022, we’ve been hard at work on adding features and functionality that continue to empower data engineers to do more with their data without needing to collect it first.
Officially Worldwide: Cribl.Cloud and Cribl Search are now available in EMEA!
At Cribl, we give the people what they want. And what they want is to keep their data close to their sources and destinations. The less data has to travel, the better — lower latency and fewer security risks. This commitment to data locality is even more pronounced among our valued customers in the EMEA region, who are enthusiastically embracing cloud-first strategies.
5 AWS Tagging Challenges - And How CloudZero Solves Them
ScienceLogic Secures the TrustRadius Best of Award in AIOps: A Triumph of Value, Features, and Relationships!
At ScienceLogic, we’ve always believed in the power of innovation and the importance of customer satisfaction. We are excited to announce that we have been honored with the TrustRadius Best of Award in the AIOps category for 2023. This is a testament to our dedication to providing exceptional value, top-notch features, and building enduring relationships with our customers.
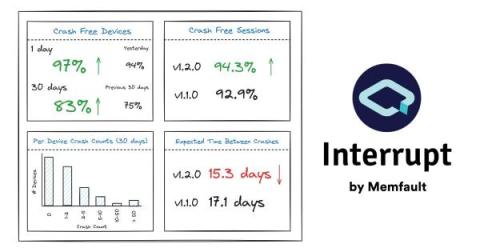
Counting Crashes to Improve Device Reliability
The first step to making reliable IoT devices is understanding that they are inherently unreliable. They will never work 100% of the time. This is partially because we firmware engineers will never write perfect code. Even if we did, our devices need to operate through various networks and gateways, such as cellular modems, mobile phone Bluetooth applications, Wi-Fi routers, cloud backends, and more, and each of these may introduce unreliability.
ITIM and the Public Sector: How Network Monitoring Rises to the Challenge
Government agencies and public sector organizations are a tantalizing hacker target. Cybercriminals go after public sector organizations because they hold confidential, often classified, information – the exact data state-sponsored and other criminal groups salivate over. The Cybersecurity and Infrastructure Security Agency, or CISA, along with the United States Computer Emergency Readiness Team, or CERT, have warned public sector IT of key threats.