Operations | Monitoring | ITSM | DevOps | Cloud
Latest Posts
Service Map & Dashboards Provide Insight into Health and Dependencies of Microservice Architecture
Dependency Confusion Attacks
You must secure your software supply chain. Now, more than ever, it is vital. For a long time, a primary concern in security was malicious actors exploiting inherent weaknesses in software. Privilege escalations, SQL injections, race conditions etc. These are, of course, still a concern and should be afforded the attention that they deserve. But now, there is another worry, one that is arguably even more important – A Supply Chain Attack.
Your guide to SSL certificates as an online customer
We’re all familiar with the internet, especially since we use it to do almost all of our daily activities. Since the days of that familiar buzzing noise of AOL dial-up as it connected to somewhere out there in the stratosphere, we’ve been hooked on the internet and its vast space that holds endless amounts of information, ready for us to tap into right at our fingertips.
Centralized Log Management for Cloud Streamlines Root Cause Analysis
Cloud services make the daily tasks of business easier. They enable remote workforce collaboration, streamline administrative tasks, and reduce capital costs. However, these “pros” come with a few “cons.” The IT stack’s increased complexity means staff work across divergent log management tools when something breaks. Centralized log management for the cloud makes root cause analysis easier by aggregating all event log data in a single location.
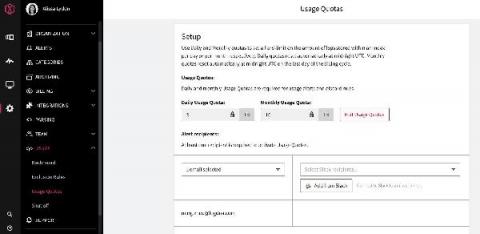
Control Your Logging Spend With Usage Quotas
We built LogDNA around the idea that developers are more productive when they have access to all of the logs they need, when they need them. However, we also know that log management can get expensive fast. And, for anyone who owns the budget for developer tools, logs can be an unpredictable line item as you try to determine your monthly, quarterly or even annual spend.
10 Server Maintenance Tips for Efficient Server Maintenance
Just like your commercial vehicles or HVAC systems, servers require regular maintenance to ensure they are operating effectively and optimally. So, we decided to compile a list of server maintenance tips you should be doing. Keep in mind, these server maintenance tips are meant to be used as a guide to help you develop your server maintenance checklist and schedule.
6 Unspoken Laws of Strategic Execution
As organizations recognize that a digital-first, contactless customer experience model is the future, they are making a considerable push towards modernizing their applications and reducing their technical debt. There are several proven techniques they can apply in order to transform their processes, technologies, and businesses.
How to use Glouton as Nagios NRPE Daemon
When using Nagios, the NRPE daemon has been the traditionnal solution to implement local checks (load, number of users, custom scripts, etc.). All other checks are performed remotely from the Nagios server. NRPE daemon has been a bit challenging as you need to keep it in sync with your Nagios server and sometimes backporting this daemon can be painful. As Glouton has been implemented in Go, when you need a Nagios NRPE daemon, you can just use the binary on any compatible system and voila.
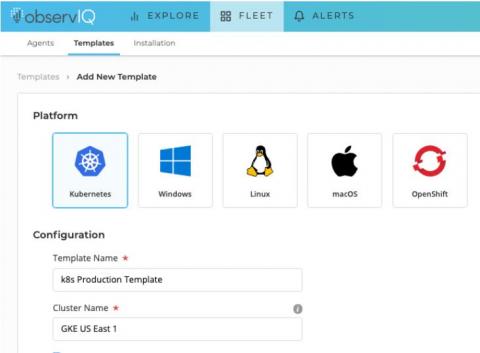
Kubernetes Logging Simplified - Pt 1: Applications
If you’re running a fleet of containerized applications on Kubernetes, aggregating and analyzing your logs can be a bit daunting if you’re not equipped with the proper knowledge and tools. Thankfully, there’s plenty of useful documentation to help you get started; observIQ provides the tools you need to gather and analyze your application logs with ease.