How to Build Custom Integrations That Help Connect OpsRamp with Other IT Operations Tools
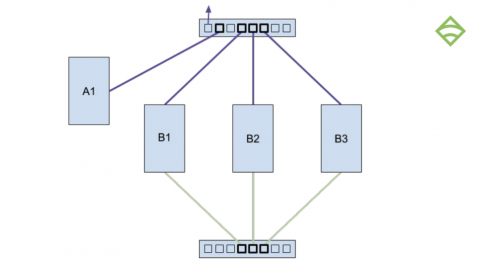
Webhooks allow third-party services to send updates through events and deliver real-time information to OpsRamp via HTTP requests. When an event gets triggered, an HTTP POST payload is sent to the configured webhook URL and custom logic associated with the webhook gets executed.