Effective Monitoring for VPN Gateways
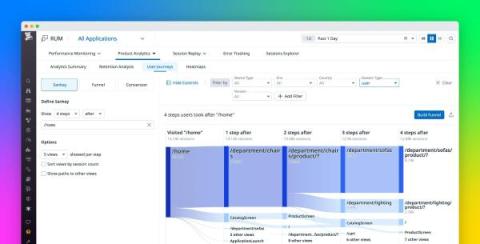
As the use of VPNs (Virtual Private Networks) becomes increasingly prevalent, ensuring their efficient, speedy, and reliable performance is crucial. Synthetic monitoring allows organizations to create simulated scenarios to evaluate and measure VPN performance, enabling them to optimize user experience and troubleshoot any issues that may arise. Exoprise provides a suite of products which work together for highly effective VPN performance gains.