Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
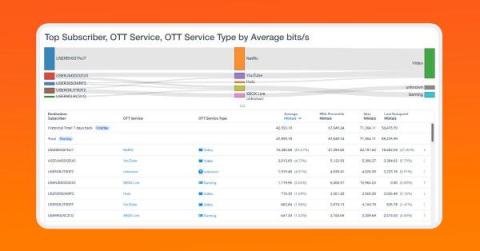
Analyzing the Traffic Patterns of Broadband Subscriber Behavior
Broadband subscriber behavior analysis is the process of collecting and analyzing data on how broadband subscribers use the internet. This data can be used to gain insights into subscriber needs and preferences, as well as to identify potential problems with the broadband service.
Network Security In an Age of Remote Work
While remote work and hybrid work have always been a thing, they've recently become more popular, and that’s created new challenges for network security. Some companies embrace remote work and/or hybrid work; some try to limit or reverse the trends. For some internal teams, remote work is easily achieved and often preferred. In other cases, in more hands-on and collaborative efforts, being physically onsite can be important.
Experience seamless Meraki network monitoring with OpManager
According to a study by Zippia, 70% of the organizations already have a digital transformation policy in place or are currently working on one. This implies the growing significance of modernization in IT. With new-age techniques such as SD-WAN, organizations can deliver an enhanced end-user experience, ensure reliable QoS, enhance their network security, optimize their network performance, and reduce their overhead costs.
What is the Purpose of Syslog Monitoring in Enterprise Software Companies?
Baseball fans know about the various in-game statistics and actions requiring someone to keep them as records. From a player's overall performance at-bat to a game's final score at the bottom of the ninth, dozens (possibly hundreds) of different statistics are happening throughout a season. In Major League Baseball, these records are essential for the team owner, front office workers and coaches to figure out strategies on the diamond or how to distribute fair pay.
What is Network Monitoring?
Today, more than ever, as IT environments become more diverse and complex, the need for an effective network monitoring solution has become paramount. However, with the digital environment, it’s constantly ever-evolving, so, these tools must keep pace with these changes to ensure they are still effective for users diagnosing issues and identifying bottlenecks within their network.
The Driving Force of Community at All Things Open 2023
The most noticeable takeaway from All Things Open 2023 was how visibly and demonstrably people were there for the event itself. Not to check a box or browse the swag but to be together, show their support of open source, and glean every last bit of knowledge they could.
Meeting the SEC's New Cybersecurity Rules: How Flowmon Empowers Public Companies To Comply
The much-anticipated cybersecurity rules by the U.S. Securities and Exchange Commission (SEC) for public companies have arrived, signaling a significant step forward from the proposed rules released in March 2022. These final rules, effective July 26, 2023, introduce new obligations that public companies must adhere to, promising a more secure and transparent corporate landscape. However, these regulations bring significant compliance challenges and litigation risks.
Got Ghosts in Your Enterprise Network?
Shining a light on the dark corners of the new enterprise network doesn't have to be as scary or overwhelming as some think. While “ghost issues” typically lurk in these sometimes unexplored places on the internet or in cloud environments, during this Halloween season your network operations teams can gain the confidence to not only uncover these network ghosts, but compel and cast them out forever.