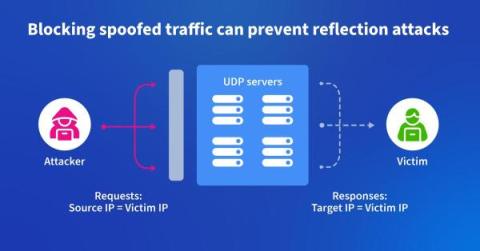
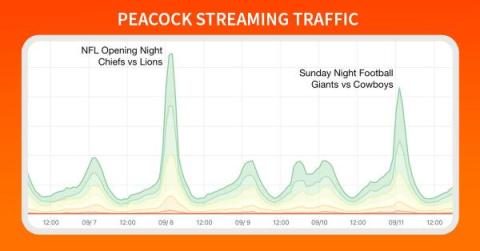
Looking back at 15 Years of Catchpoint and Internet Performance History
Fifteen years ago, the Internet was a very different place. It operated on a very different scale, had different market leaders and it faced different technical challenges. What has not changed, however, is the need for the best – indeed ever higher - performance and resilience. We founded Catchpoint in September 2008 (amid terrible economic conditions) with the desire to make the Internet better. Not exactly the greatest year to launch a startup.