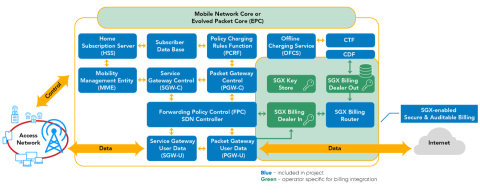
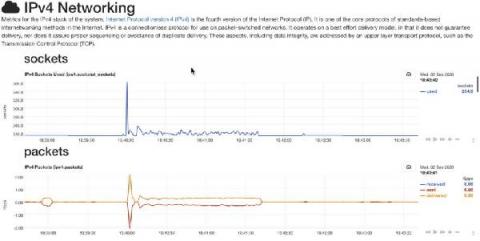
Evolution of Open-source EPC - A Revolution in the Telecom Industry
Open-source projects gravitate to some common problems in the industry. The use of open-source projects accelerates product/solution development and cuts down the costs. Open-source projects for embedded systems to the cloud are commonplace.