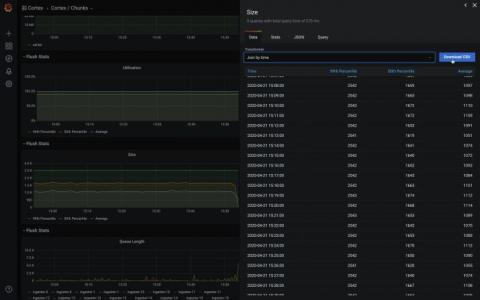
Grafana 7.0 sneak peek: Inspect drawer lets you get raw data and download as CSV
Grafana v7.0 is coming soon! Here’s another sneak peek of one of its features: the inspect drawer. The inspect drawer is a feature that every panel will support, including internal as well as external community plugins. In this new drawer, you will be able to view the raw data in a table format, apply some predefined transformations, and download as CSV. “Download as CSV” previously only existed as a custom feature for the Graph & Table panel.