IT security: Disrupting the cybersecurity kill chain by detecting domain reconnaissance
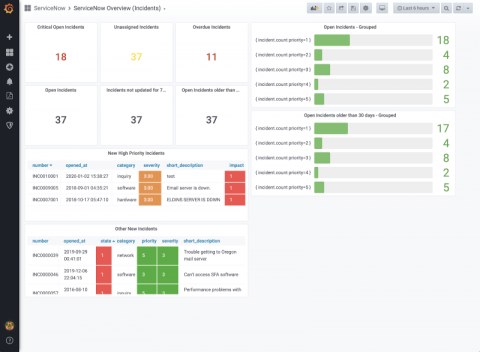
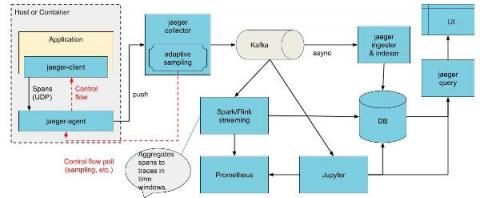
Cyberattacks are a growing threat, and organizations are investing time and money in security strategies to make certain that their infrastructures are secure. Active Directory (AD) is a constant target for compromise, as it’s at the core of any organization’s security — it handles authentication and authorization for all users in an organization.