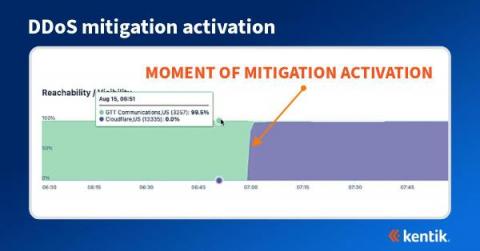
Jason Chan on Harnessing Security Automation to Manage Cyberthreat Complexity
Torq is extremely proud to have Jason Chan on our advisory board. Jason has more than 20 years of experience working in cybersecurity. He’s one of the world’s leading experts in adopting security automation, cloud security, and enhancing security in modern software development practices. Jason’s most recent career experience was leading the information security organization at Netflix for more than a decade.