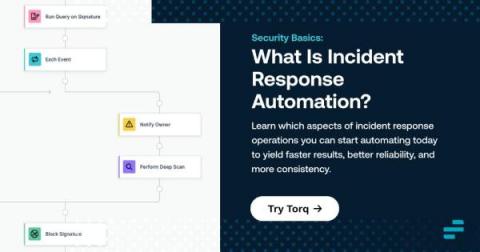
Accessing CFEngine nightly packages
Did you know that nightly builds of CFEngine are available? cf-remote is the most convenient way to get nightly packages. If you’re not familiar with it, or if you need a refresher, check out our other blog posts about cf-remote.