Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
The importance of behavior analytics in your organization's cybersecurity
Collin’s dictionary defines “behavior pattern” as a recurrent way of acting by an individual or group toward a given object or in a given situation. Analyzing and understanding the behavior patterns of individuals has proven to provide in-depth solutions to problems in different walks of life, including cybersecurity.
Ensuring compliance with DISA STIGs, NIST 800-53, CMMC, and RMF
This blog is the second in a four-part series on infrastructure automation for government agencies that are modernizing digital systems while grappling with budget and staffing constraints and the challenges of COVID-19.
Long Weekend and you Locked Yourself Out of Your Computer
The latest Verizon DBIR report is out and we all should realize, normal is not the new workplace. Picture this: You’re logging into the work account after a long weekend of gratitude, remembrance and maybe even getting to hug someone safely. Okay, we’re exaggerating a little but variations of this scene are playing out all over the country this week. You’re frustrated and you haven’t even gotten started on the work that piled up over the weekend.
Google Authenticator and Pandora FMS, defend yourself from cyberattacks
For a long time, the Internet has been an easily accessible place for most people around the world, full of information, fun, and in general, it is an almost indispensable tool for most companies, if not all, and very useful in many other areas, such as education, administration, etc. But, since evil is a latent quality in the human being, this useful tool has also become a double-edged sword.
Understanding Splunk Phantom's Join Logic
If you’re an active Splunk Phantom user, it’s safe to assume you know what a playbook is. If not, here’s a quick summary: Phantom playbooks allow analysts to automate everyday security tasks, without the need for human interaction. Manual security tasks that used to take 30 minutes can now be executed automatically in seconds using a playbook. The result? Increased productivity and efficiency, time saved, and headaches avoided.
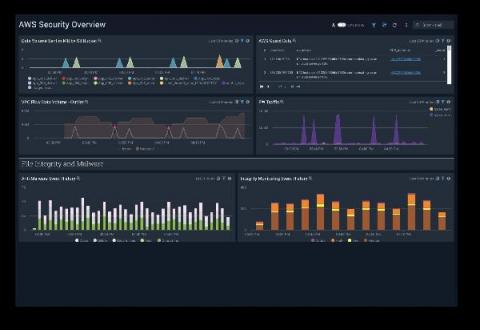
Introducing Sumo Logic Cloud SIEM powered by AWS
How to Proactively Plan Threat Hunting Queries
As your security capabilities improve with centralized log management, you can create proactive threat hunting queries. Setting baselines, determining abnormal behavior, and choosing an attack framework helps you mitigate risk and respond to incidents. To reduce key metrics like the mean time to investigate (MTTI) and mean time to respond (MTTR), security operations teams need to understand and create proactive queries based on their environments.
Going Beyond Exclude Patterns: Safe Repositories With Priority Resolution
Easily Automate Across Your AWS Environments with Splunk Phantom
When running Splunk Phantom with AWS services, it can be tricky to make sure Splunk Phantom has the right access. When you’re managing multiple AWS accounts, the effort to configure Splunk Phantom’s access to every account can feel insurmountable. Fortunately, Amazon has the Security Token Service to solve this problem with temporary credentials, so we’ve integrated it with Splunk Phantom!