Threat Hunting with Cribl Search
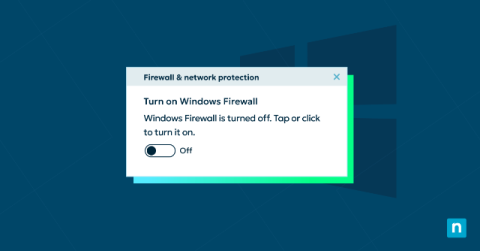
Imagine you’re the protector of a castle. Your walls are tall, the gates are strong, and the guards are well-trained. But what if an intruder was still able to slip past your defenses? Even with the best security tools, not every threat will be caught. Threat hunting is the proactive approach to finding attackers that might have bypassed your defenses.