Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
Survey: Remote Work Leads to Increase in Security Issues
Over the past several months, the world has changed as we know it. The COVID-19 pandemic has transformed the way many companies do business, with more virtual events, video calls, and curbside pickups than ever before. Although challenging at times—we miss attending live events and other social activities—this pandemic has forced many companies to think outside of the box. The traditional ways of doing business were no longer feasible or even legal in some cases.
I Can See Securely Now
Pretty much every organization of any size is paying close attention to the adoption of security practices in order to manage and protect their most sensitive data, including personal identifiable information (PII), personal health information (PHI), or other customer and financial data. For any team using SaaS tools, data protection is a table-stakes requirement. For compliance regulated industries — banking, financial services, healthcare.
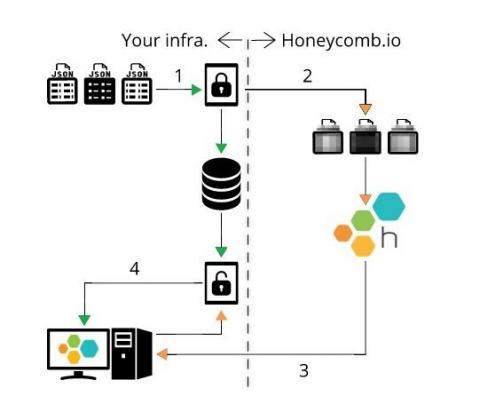
Integrate your IDS + monitoring with the Sensu Tripwire asset
Tripwire, created by our friend Gene Kim, is a popular intrusion detection system (IDS) with both commercial and open source offerings. As a fun side project, I put together a Tripwire asset for Sensu. While this is more a prototype than anything else, I wanted to take this opportunity to offer some background on IDS, Tripwire, and integrating intrusion detection into your monitoring workflow, with the overall aim of illustrating how easy it is to deploy solutions with Sensu.
Orchestration and Automation Helps Defense, Intelligence Personnel Tackle Higher-Level Tasks
What if you could get your hands on a force multiplier that got rid of the repetitive, routine work that was tying down your team, got more productivity out of your assembled work force, and gave everyone a more challenging, meaningful to-do list that made better use of their knowledge, experience, and passion?
Five worthy reads: Privacy in pandemic management
Five worthy reads is a regular column on five noteworthy items we have discovered while researching trending and timeless topics. This week, we explore the data privacy challenges and concerns that have arisen during the COVID-19 pandemic. In the wake of COVID-19, the world has witnessed the power of technology.
Ways to Ensure App Security With Java Features
As important as adding new features, app developers need to start placing more emphasis on the security aspect of the applications they design. After all, more app features mean more data residing within an app. Without proper security controls in place, that data can be vulnerable to intruders.
Maximizing Your Splunk Investment: Introducing Splunk Lantern
Congratulations, you just bought Splunk! You made a great decision, and now it's time to start solving all those business problems on your plate. Maybe you are trying to reduce the time spent managing cyber risks from hours to minutes. Or you might be executing a digital transformation of your customer experience. Or perhaps you are trying to save $70 million dollars in an IT consolidation project. But you have just one question: how?
Okta Log Insights
This post will show you how Coralogix can provide analytics and insights for your Okta logs, both performance, and security. Okta is one of the leading Identity provider platforms in the world, offering a variety of cloud services including a Single Sign-On solution to manage and secure company user authentication with 3rd party applications.
CFEngine in a High Performance Computing environment
In High-Performance Computing (HPC) uptime and performance are very important. HPC is an area of computing that often focuses on research and development, supporting teams with extremely complex problems they need to solve, and heavy computation mathematical problems, such as protein folding for vaccine development. To achieve this, HPC systems rely on high performance, the equipment is expensive, and the average customer has very high demands.